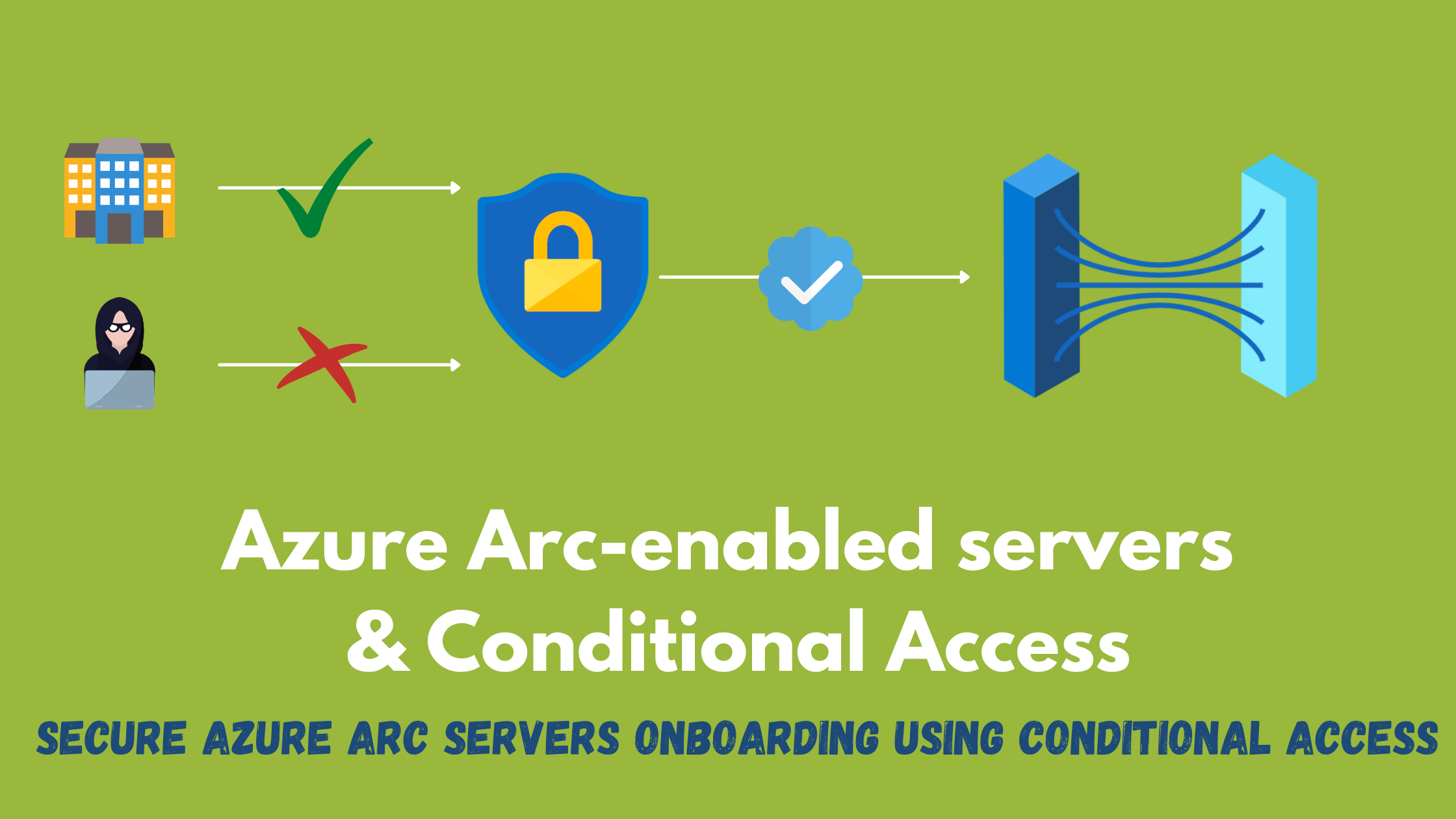
Secure Azure Arc servers onboarding using Conditional Access
One of the most common methods of onboarding servers to Azure Arc is using a short-lived service principal with least privilege (using the Azure Connected Machine Onboarding role), yet there can be some concerns around having this service principal’s identity compromised specially if it’s not recycled frequently, where an attacker can use it to onboard other servers outside of your organization.
Recently it was announced in Ignite 2021, that Conditional Access policies (In Preview) can be now applied to not only users but also workload identities. This allows applying Conditional Access policies to service principals which adds great flexibility to better secure your identities. In this post, I will test this new capability to only allow Azure Arc onboarding from within one location and block any other attempts to onboard originating from outside of this trusted location.
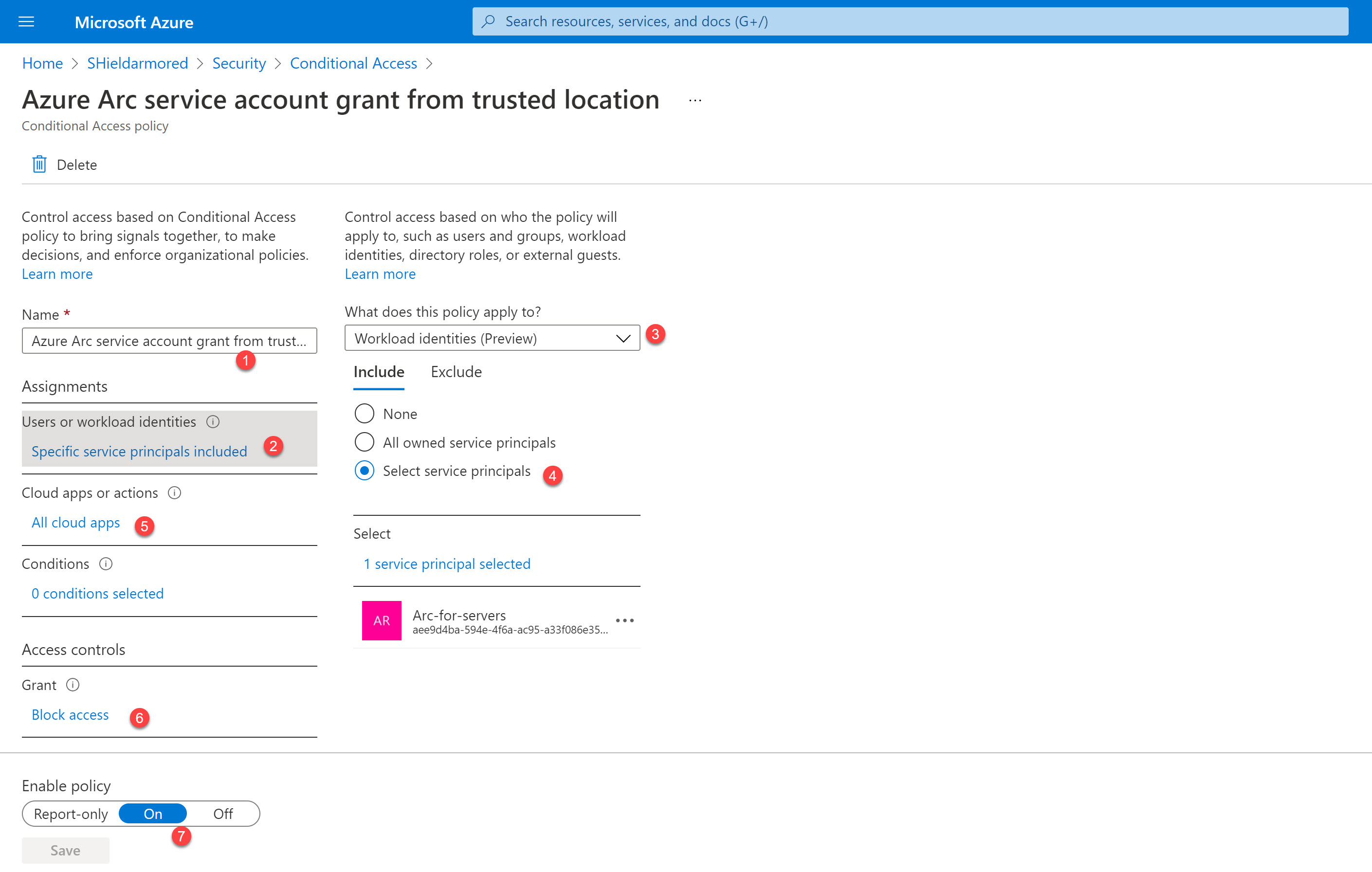
Block Azure Arc onboarding service principal
First, I will create a policy to block the service principal to demonstrate how this feature will work.
- Create a new Conditional Access policy
- Select Workload identities in the assignments section
- Select the service principal I already created for Azure Arc-enabled servers onboarding
- Select All cloud apps in the cloud apps section
- Select Block Access in the access controls section
- Enable this policy
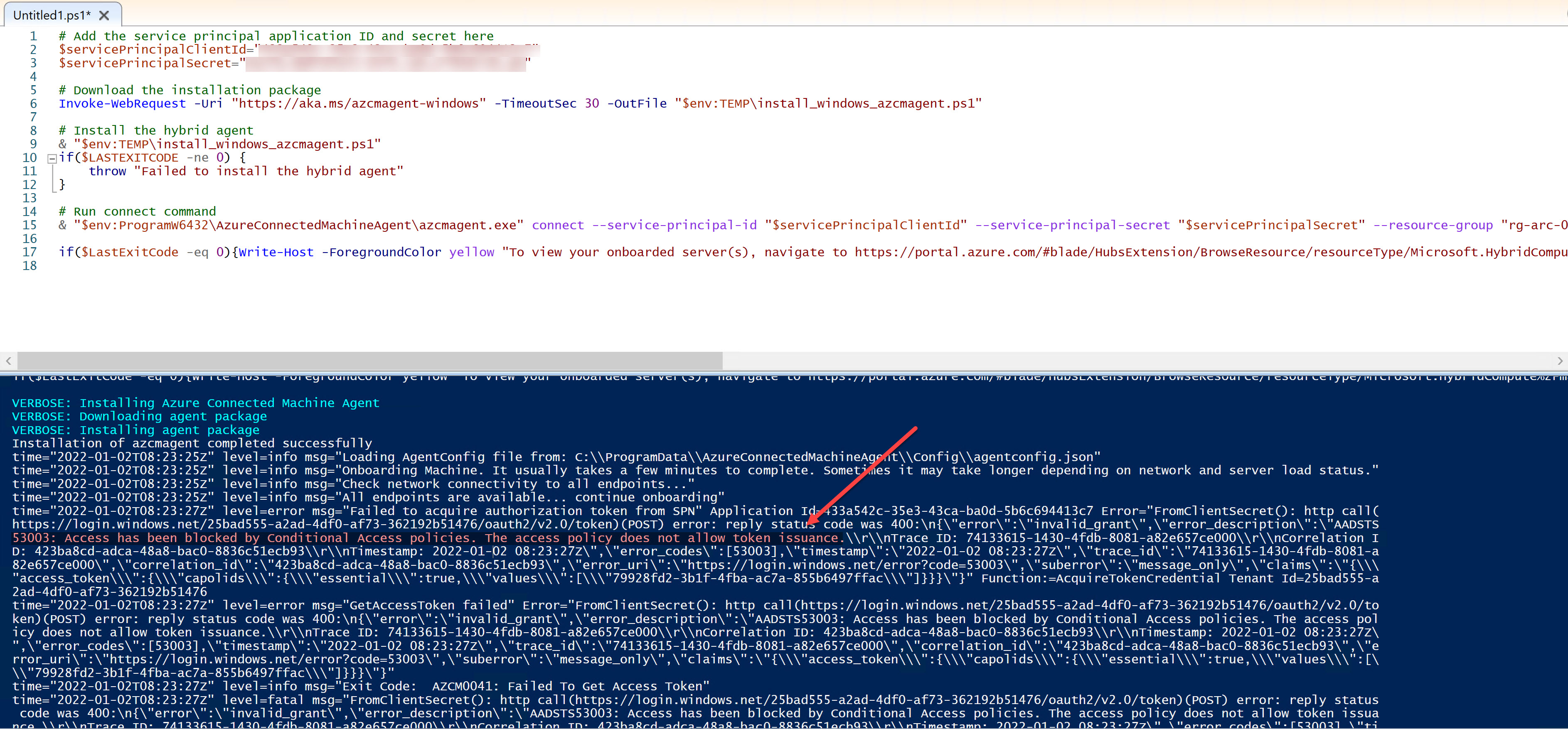
- Now trying to onboard a server using this service principal, I get an error that a Conditional Access policy has blocked this request.
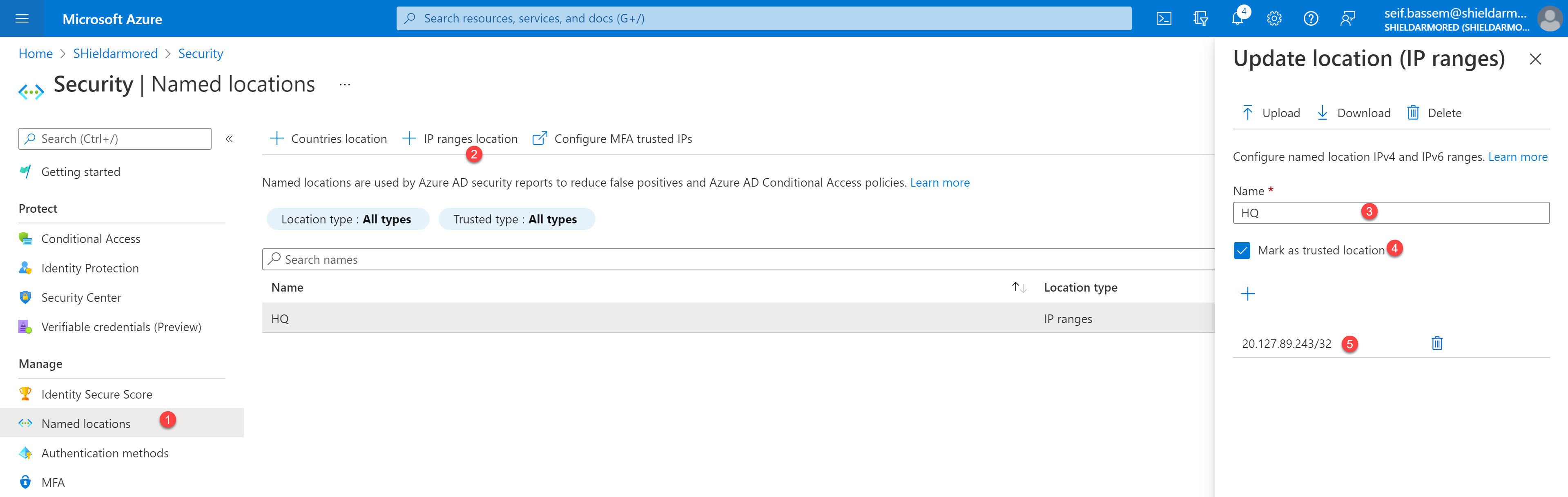
Allow Azure Arc onboarding only from trusted locations
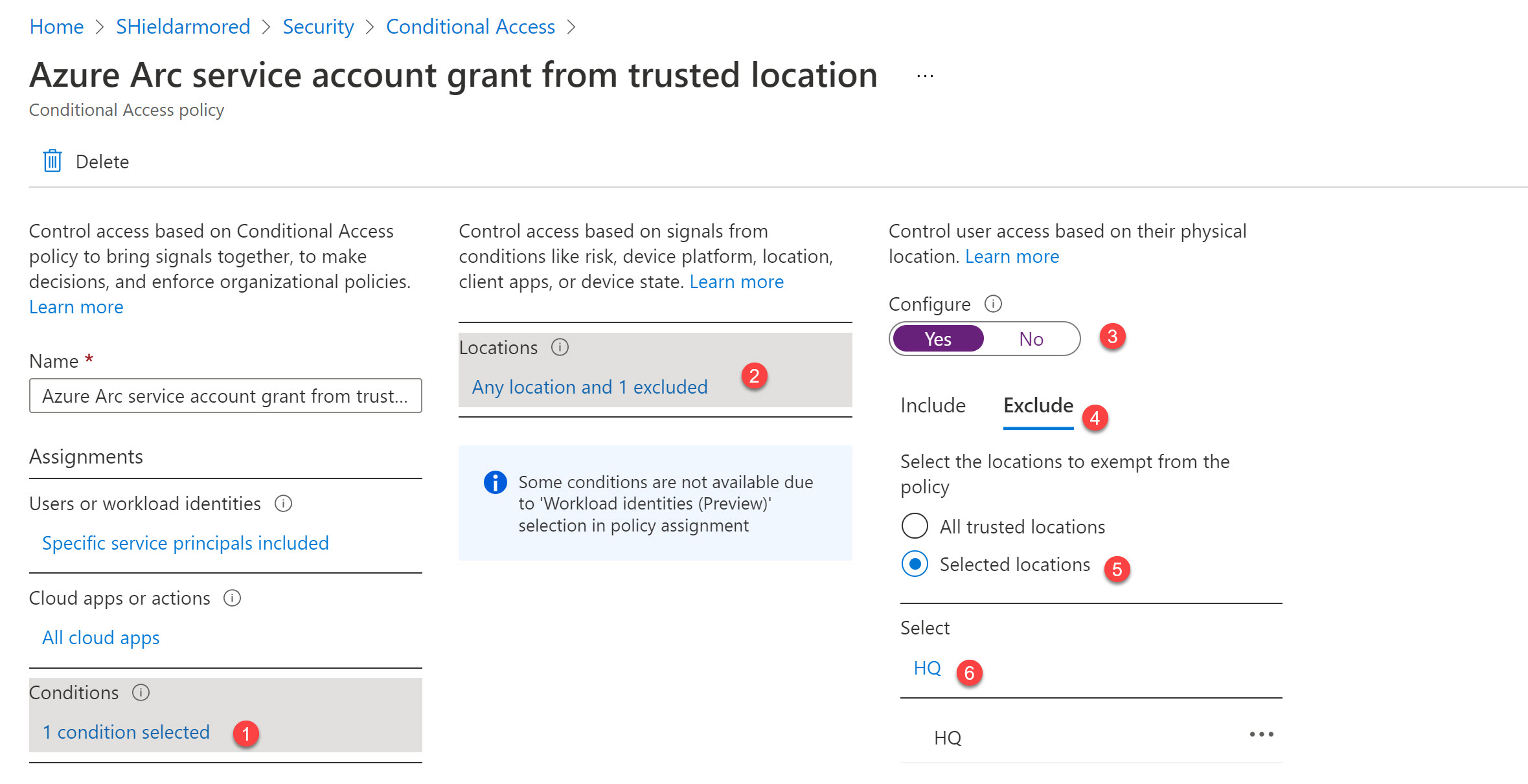
Next, I will create a new trusted location and add it to the policy to only grant access for this service principal from a specific IP range.
Create a new IP ranges-based named location and add your datacenter(s) IP ranges and mark them as a trusted location
In this example, I only added one IP address as a named location but you can add IP ranges or countries to the list. More information can be found here.
Edit the Conditional Access policy and add a condition to block all locations except for the trusted ones.
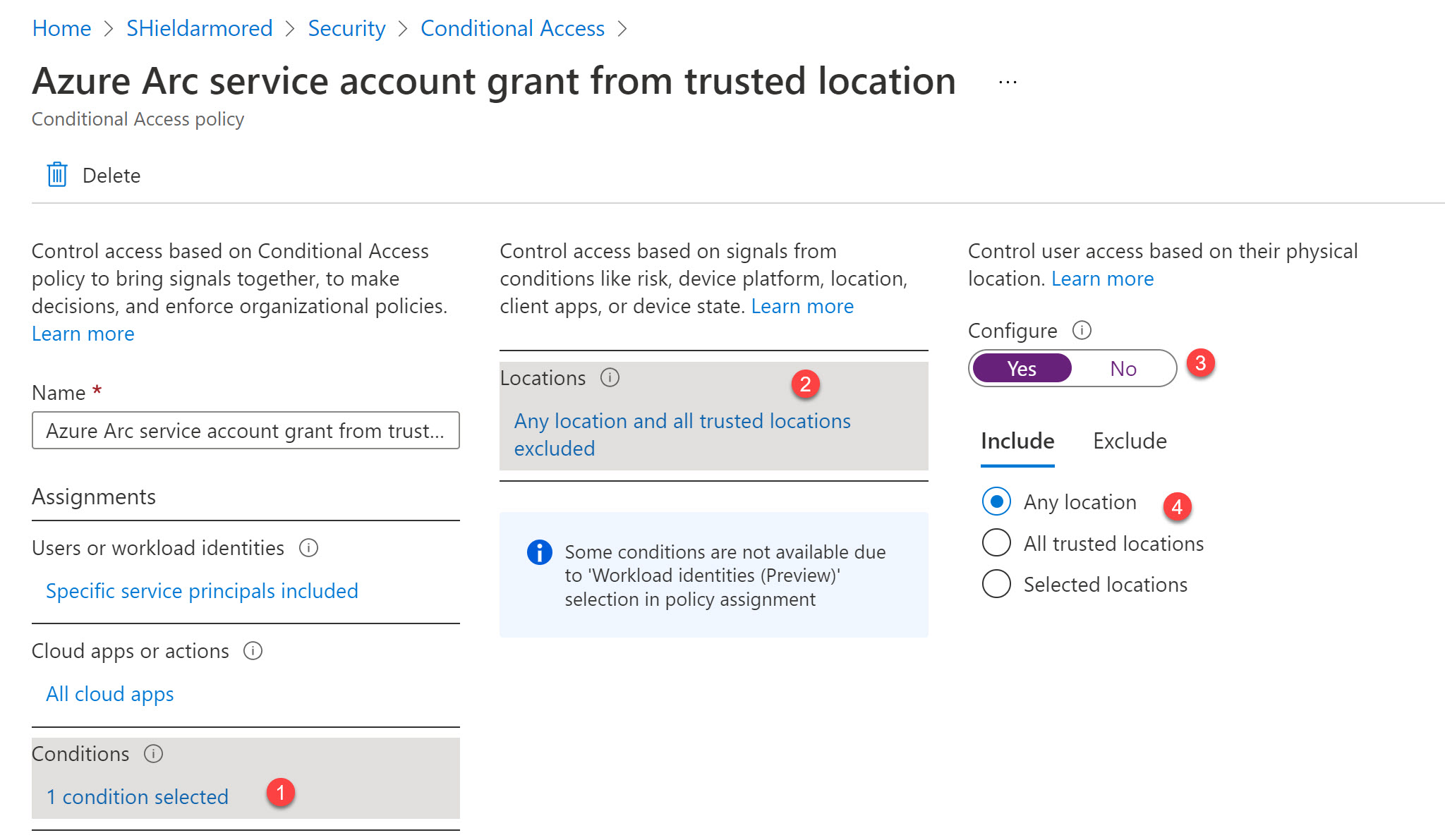
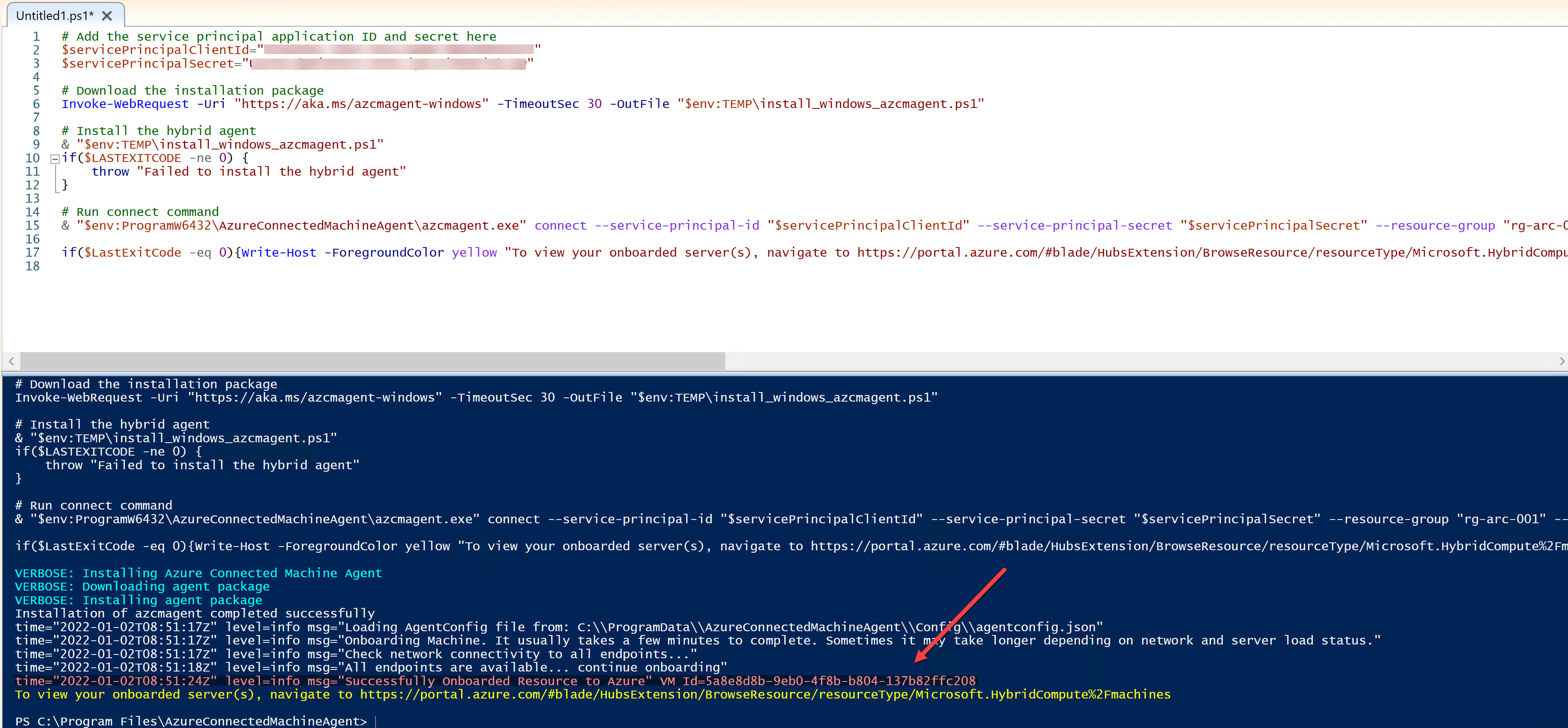
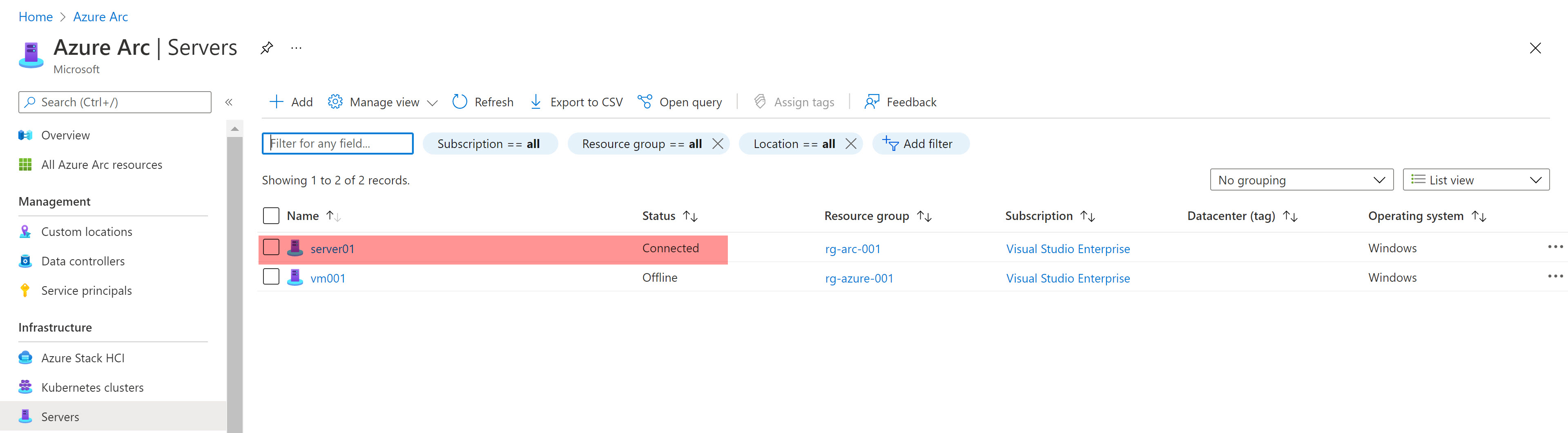
Now, attepmting to onboard again, everything works smoothly and the server gets onboarded successfully.
You May Also Like
Azure Arc Onboarding using Endpoint Configuration Manager
Azure Arc-enabled servers allows you to project your hybrid servers …
Automate non-Azure servers with Azure Arc-enabled servers
Azure Arc-enabled servers allows you to project your hybrid servers …
Deploy Azure App Services anywhere using Azure Arc
At the date of this post, Azure has 60+ regions around the world where …