Improving your security posture with Governance Rules
Microsoft Defender for Cloud analyzes your resources on a regular basis to identify potential security misconfigurations and weaknesses. It then provides detailed recommendations on the risks of those misconfigurations and actionable guidance on how to remediate those issues. Those recommendations would add up to your secure score where you can track your progress and compliance. One missing piece with this great feature is how to orchestrate assignment, tracking and reporting the progress of the remediation of those recommendations.
A new feature has been recently introduced to allow you to assign owners to recommendations based on severity or type and designate a deadline for remediation, in addition to a report to have full visibility on remdiation timelines. This feature is called Governance Rules and in this post, I will give it a spin.
Governance Rules
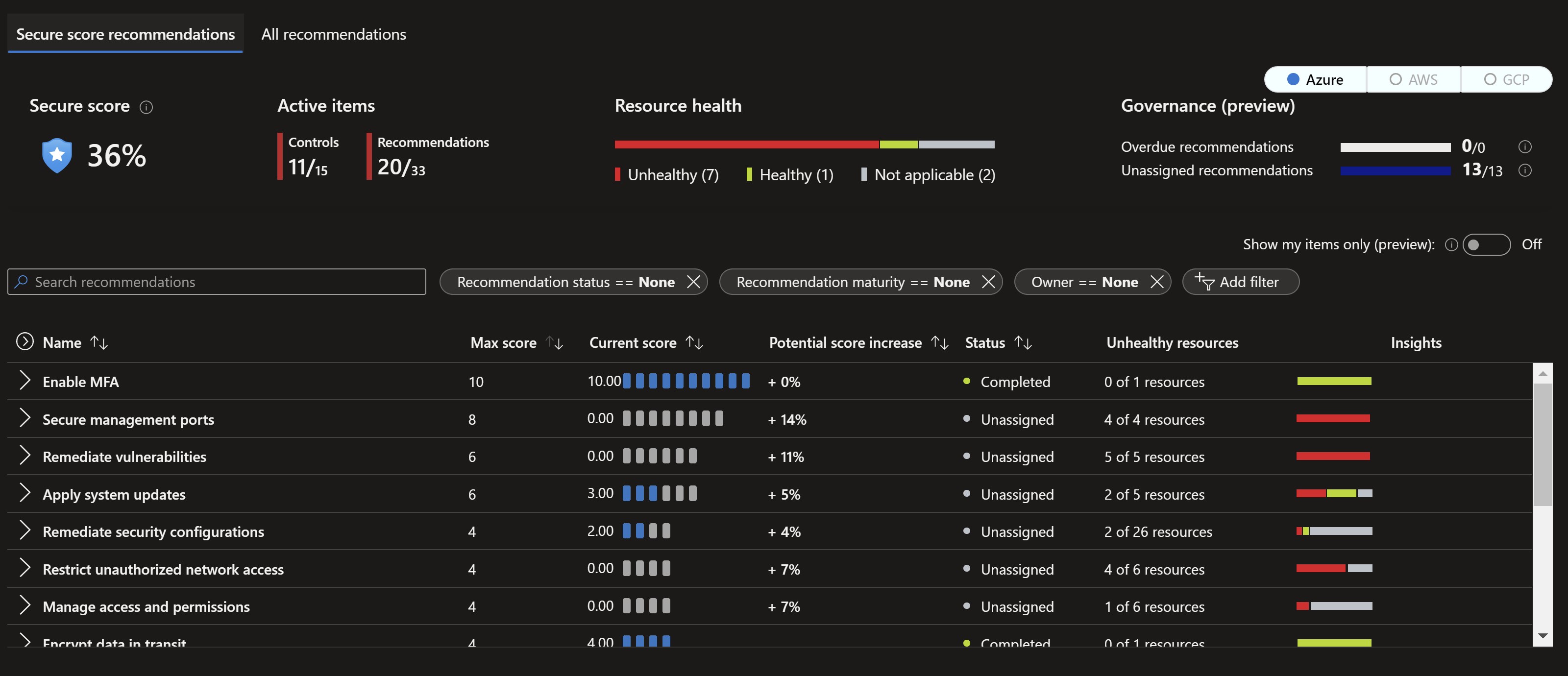
Looking at first at my current environment, I have a secure score of 36% with lots of recommendations.
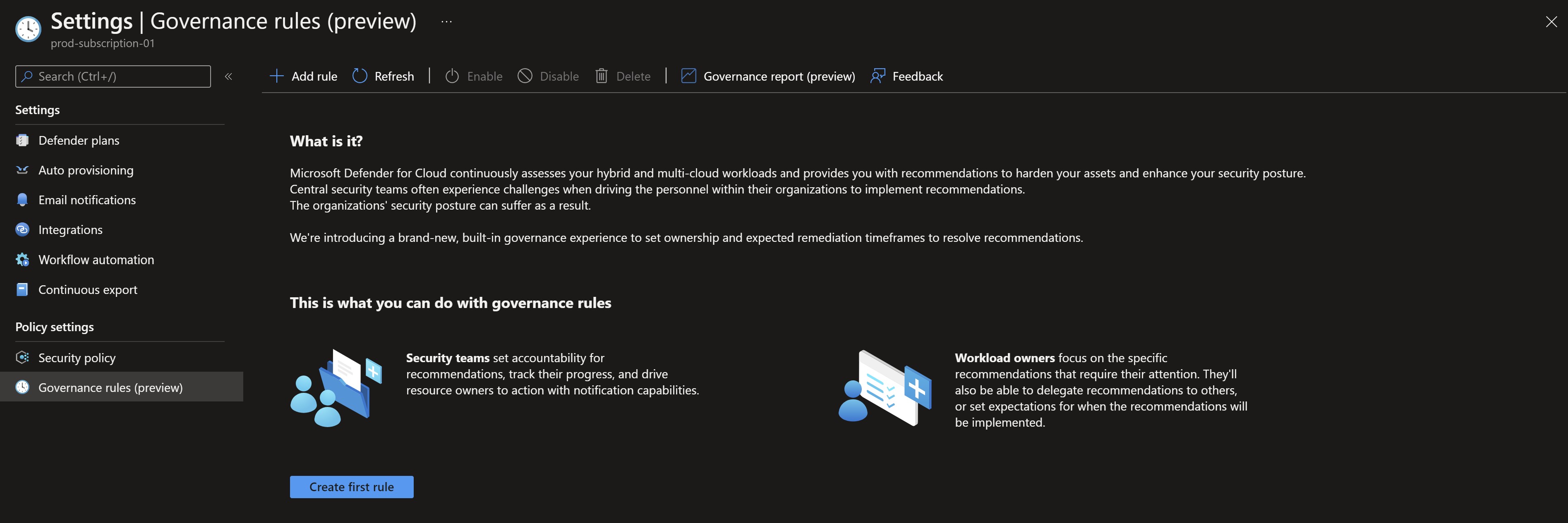
If we go to the Defender for Cloud settings, we can see the new Governance Rules feature.
Let’s try to create a new rule, give it a name, a description and explore the options available
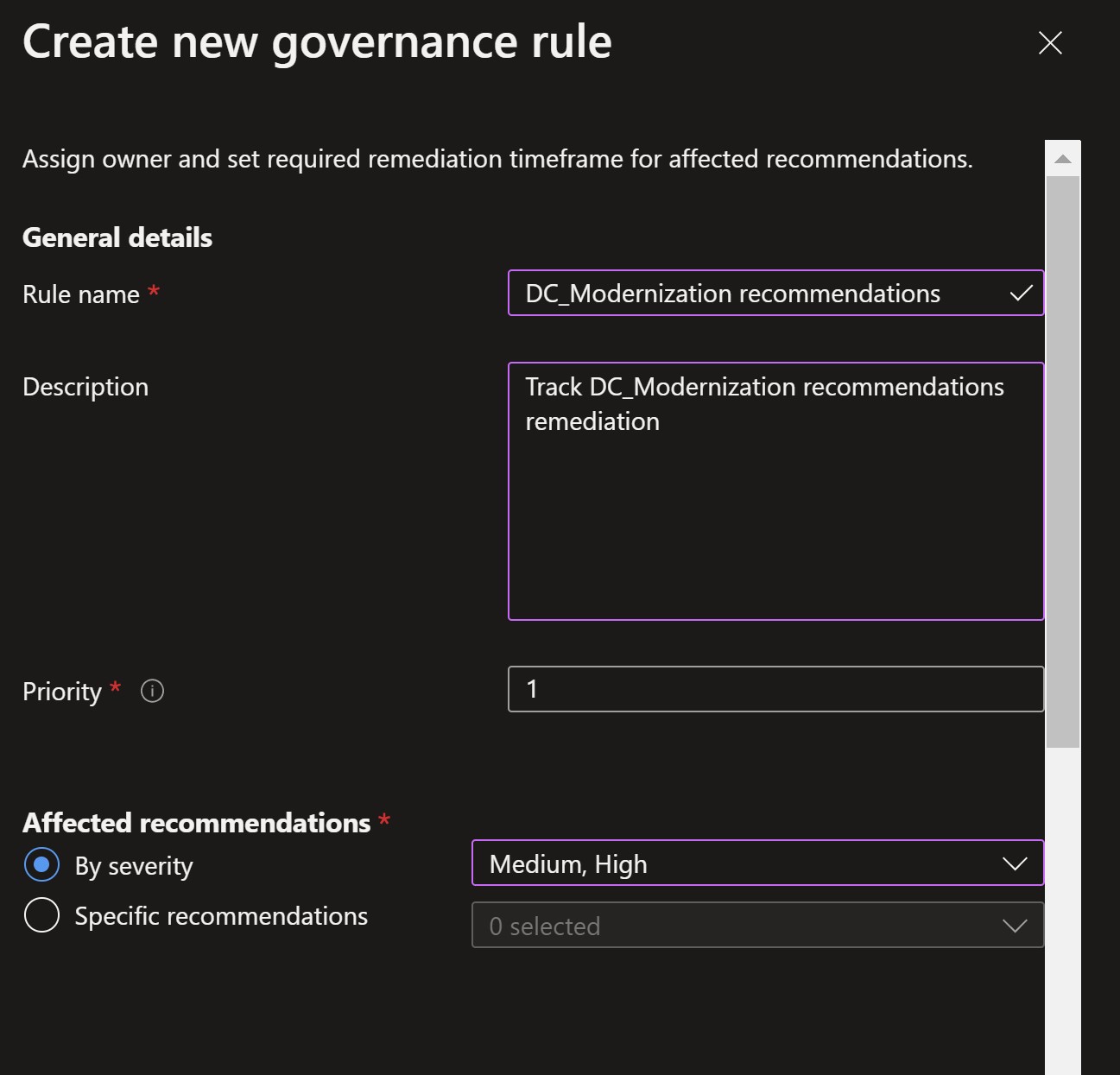
Affected recommendations: I will select the High and Medium severities so that this rule only applies to recommendations with those severity levels. We can alternatively manually select the exact recommendations from the list.
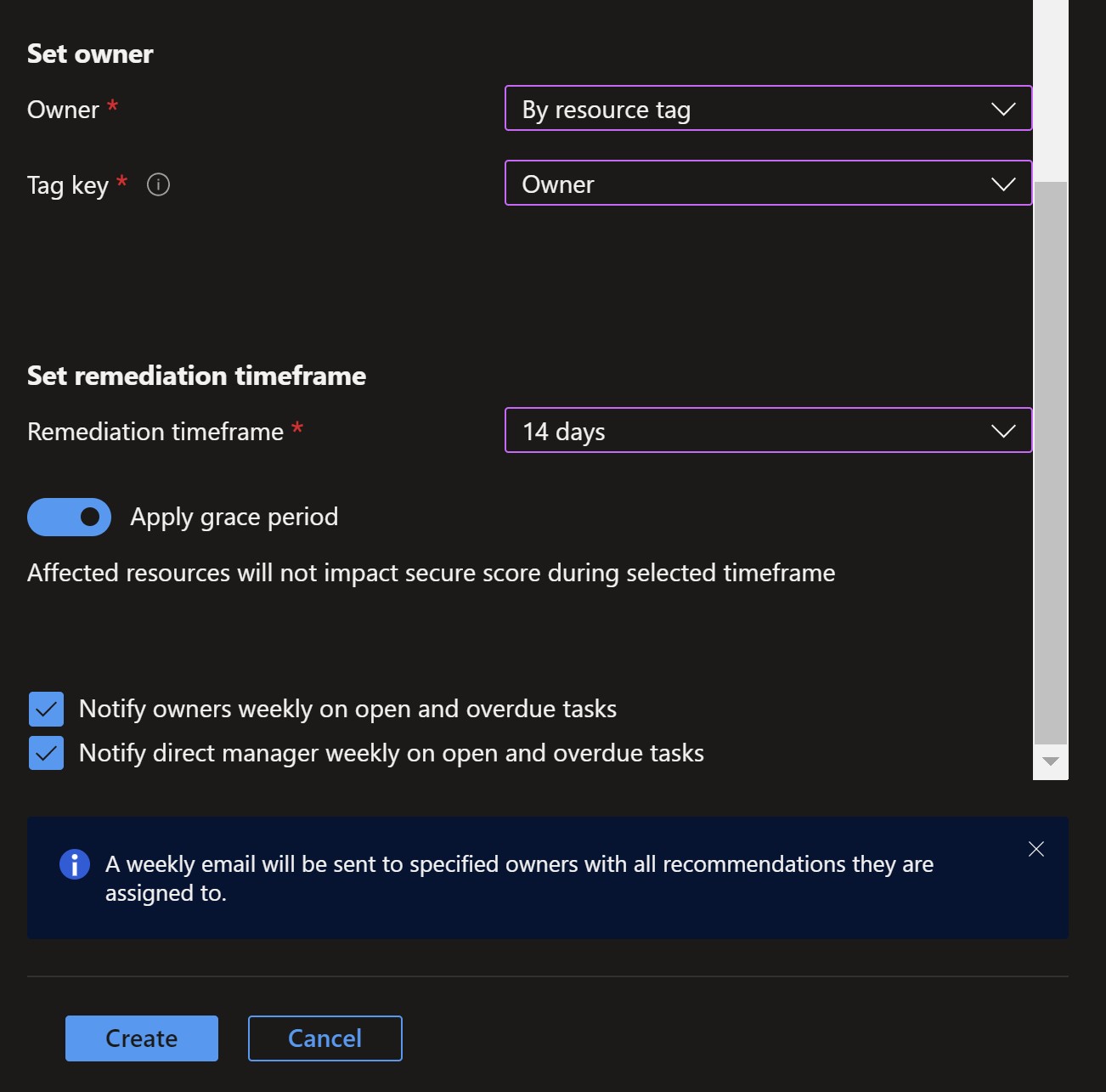
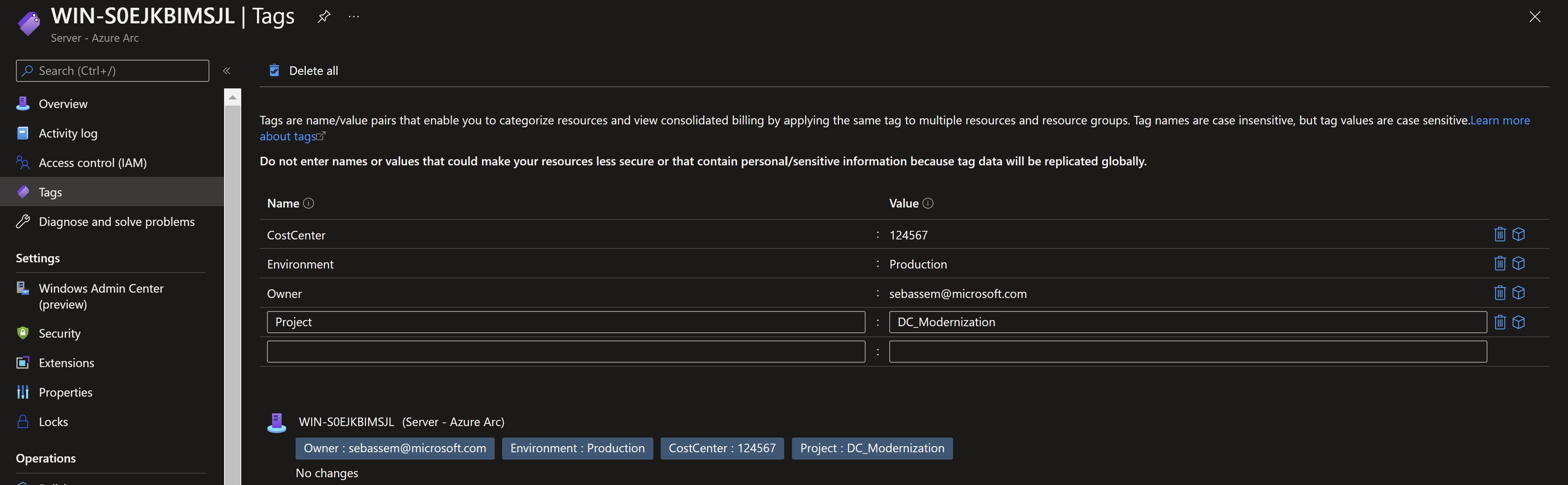
Owner: we can type in an email address or have it populated automatically if we have the right tag applied to the resources. I already have an owner tag assigned to one of the affected resources.
Remediation timeframe: This will be the time it should take the owner to remediate this recommendation. We can choose to apply a Grace Period which would make this recommendation not to have an effect on our total secure score till the allocated timeframe expires.
Notification: Here we can select if there should be a weekly summary email to the owner and their manager (populated from Azure AD) for open items.
Finally, we have our governance rule all set and ready. Immediatley, we get a popup saying that our rule matches some existing recommendations.
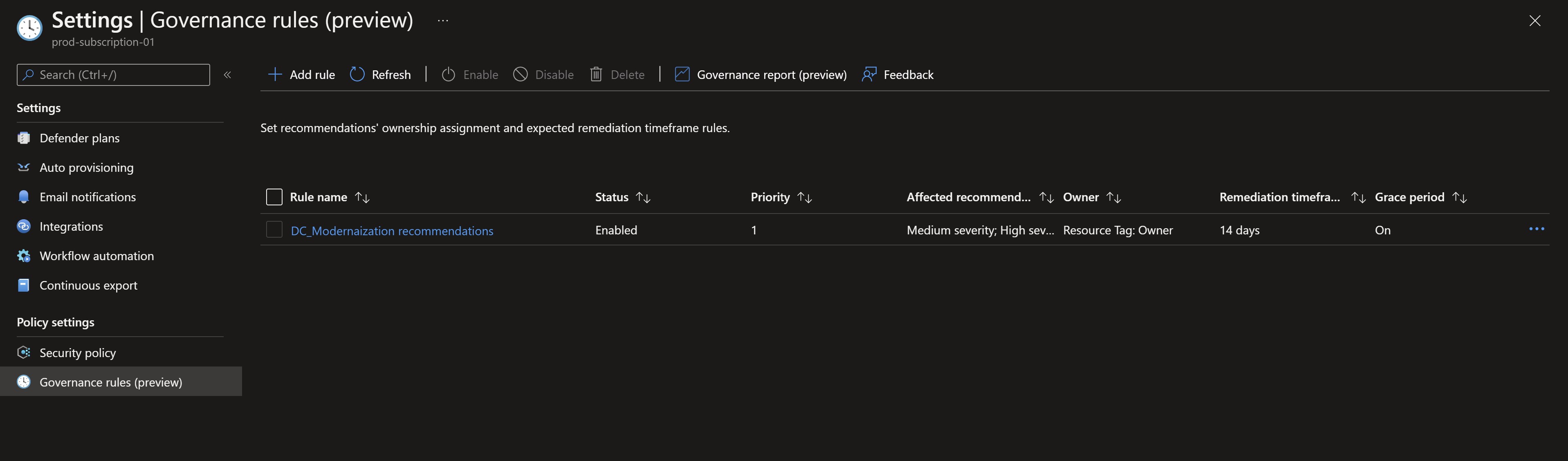
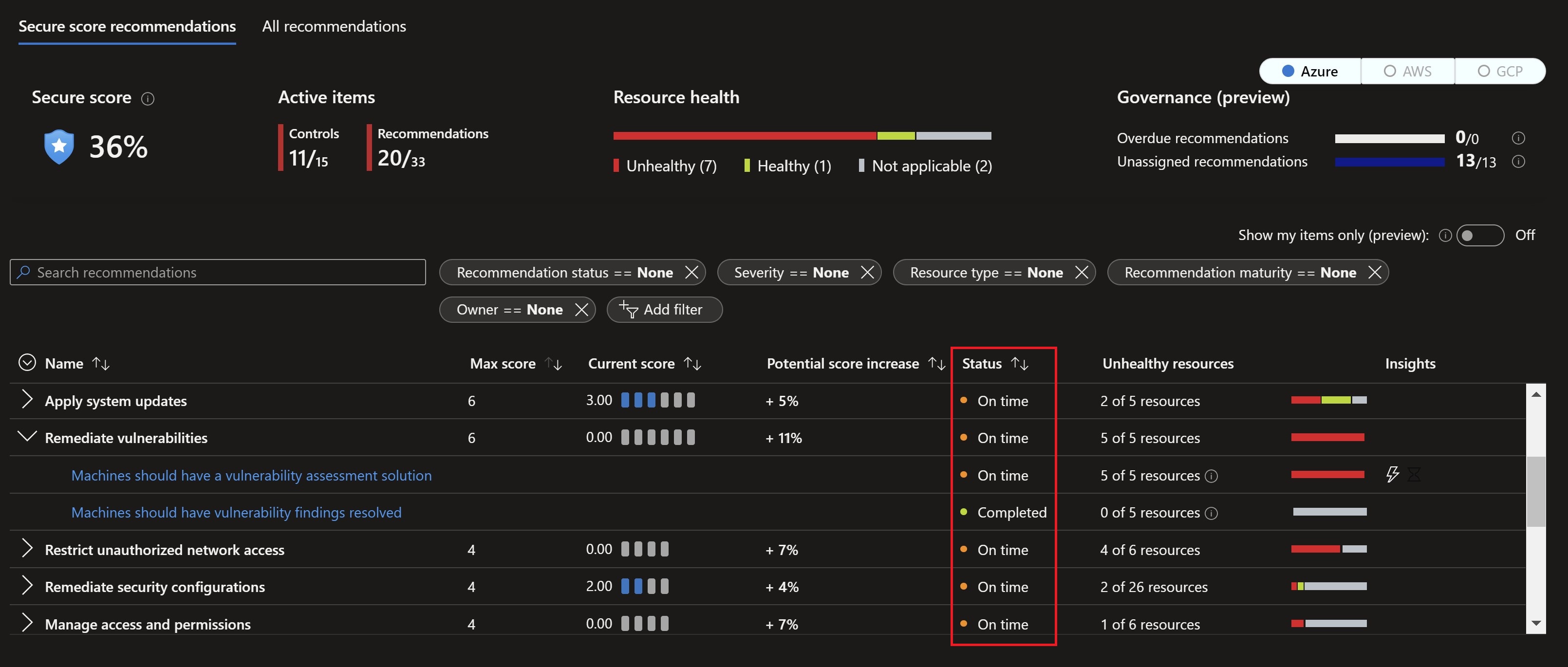
Navigating back to the Defender for Cloud portal, we can see the status column showing different statuses like On time which means the rule applies to them since they have either medium or high severity.
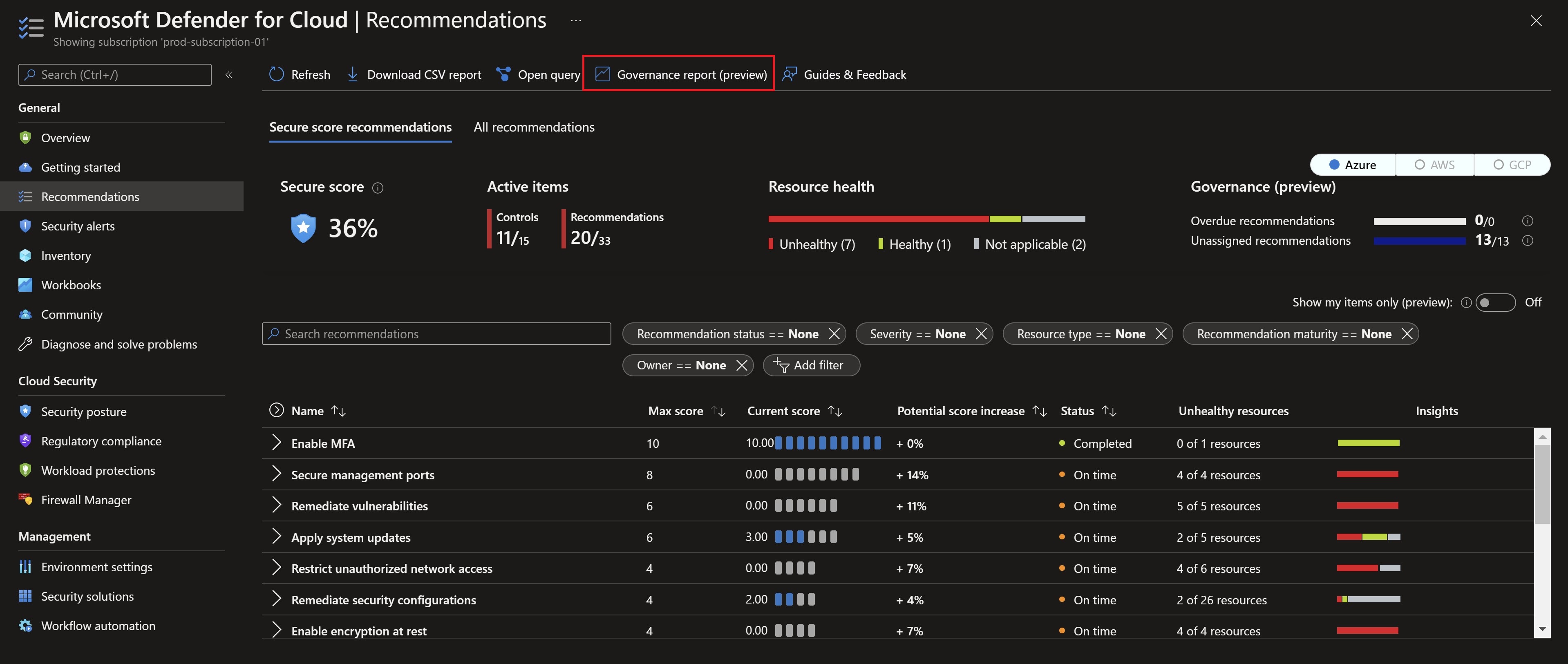
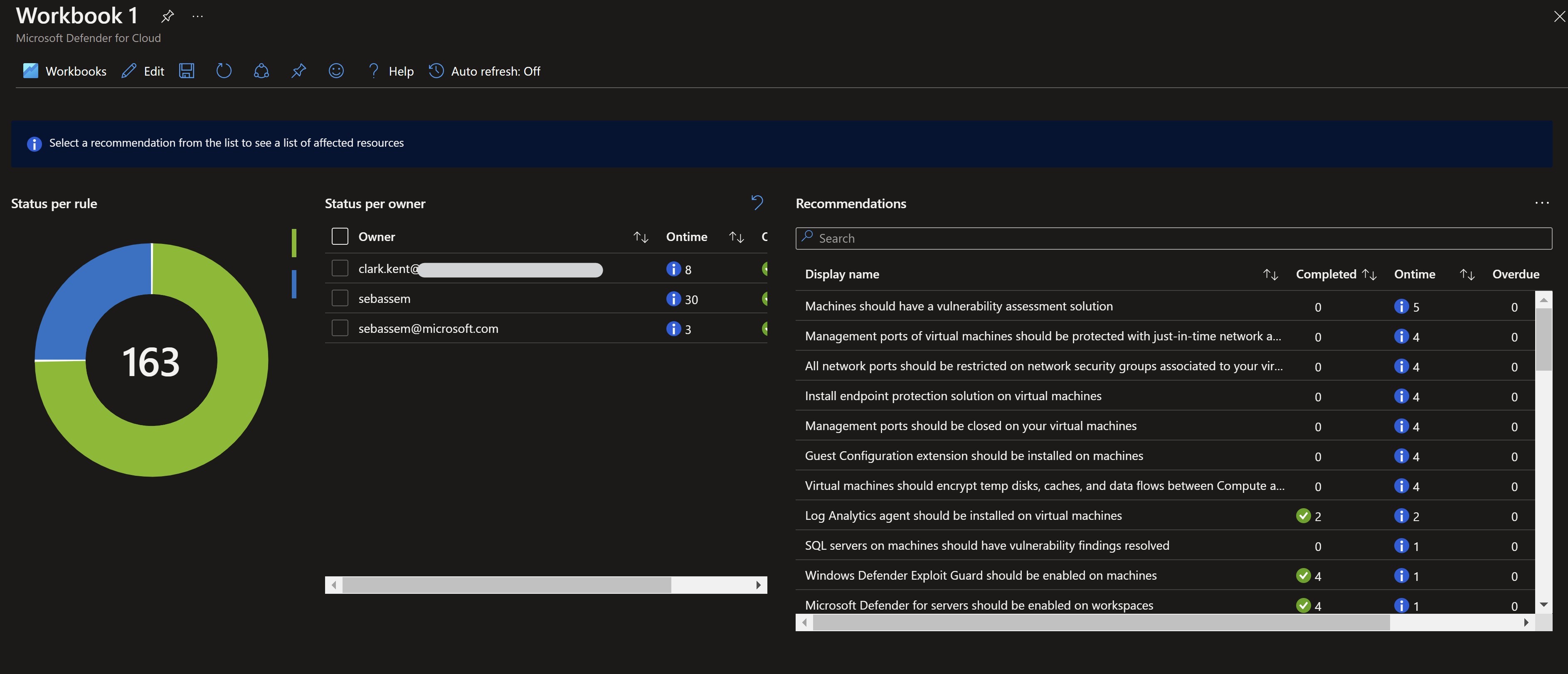
We can also see a new Governance report button at the top which would take us to a really nice workbook that help us keep track of all work being done on the remediation process.
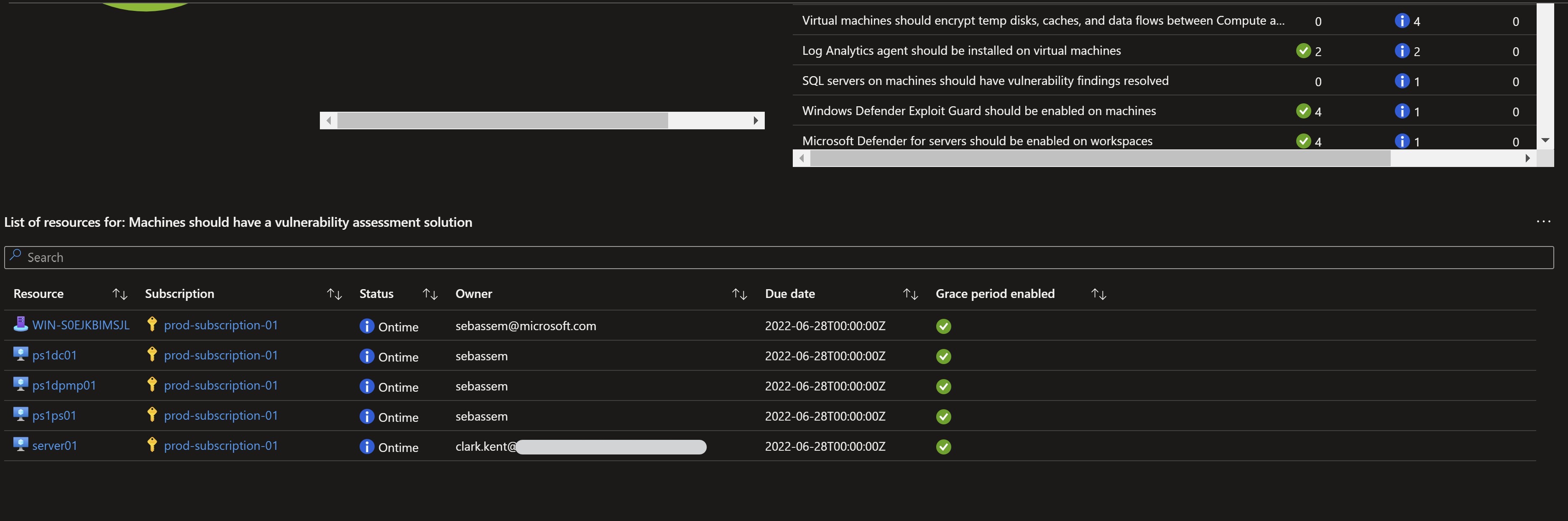
Remember, the grace period option we specified ? After checking the secure score in 24 hours, I can see now that the score has changed since all the high and medium recommendations which are within the timeframe will not add up to the score.
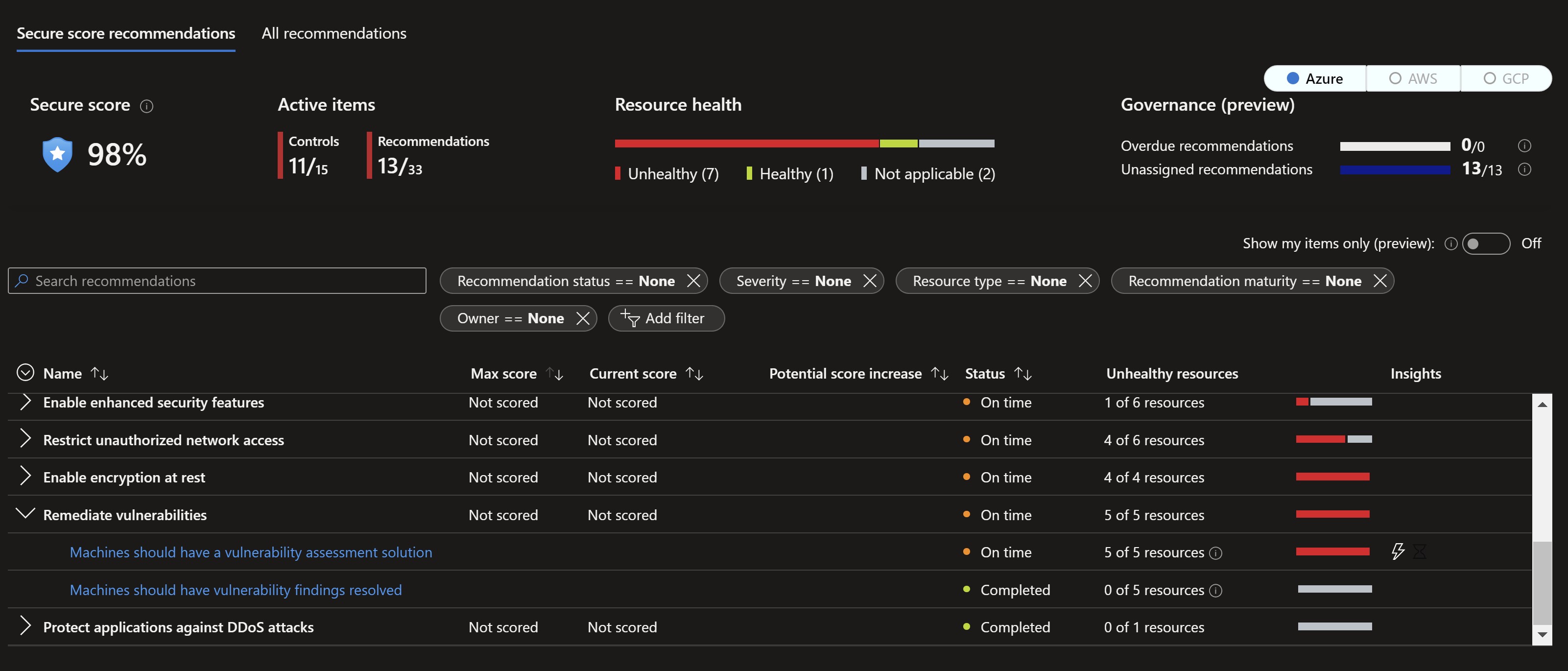
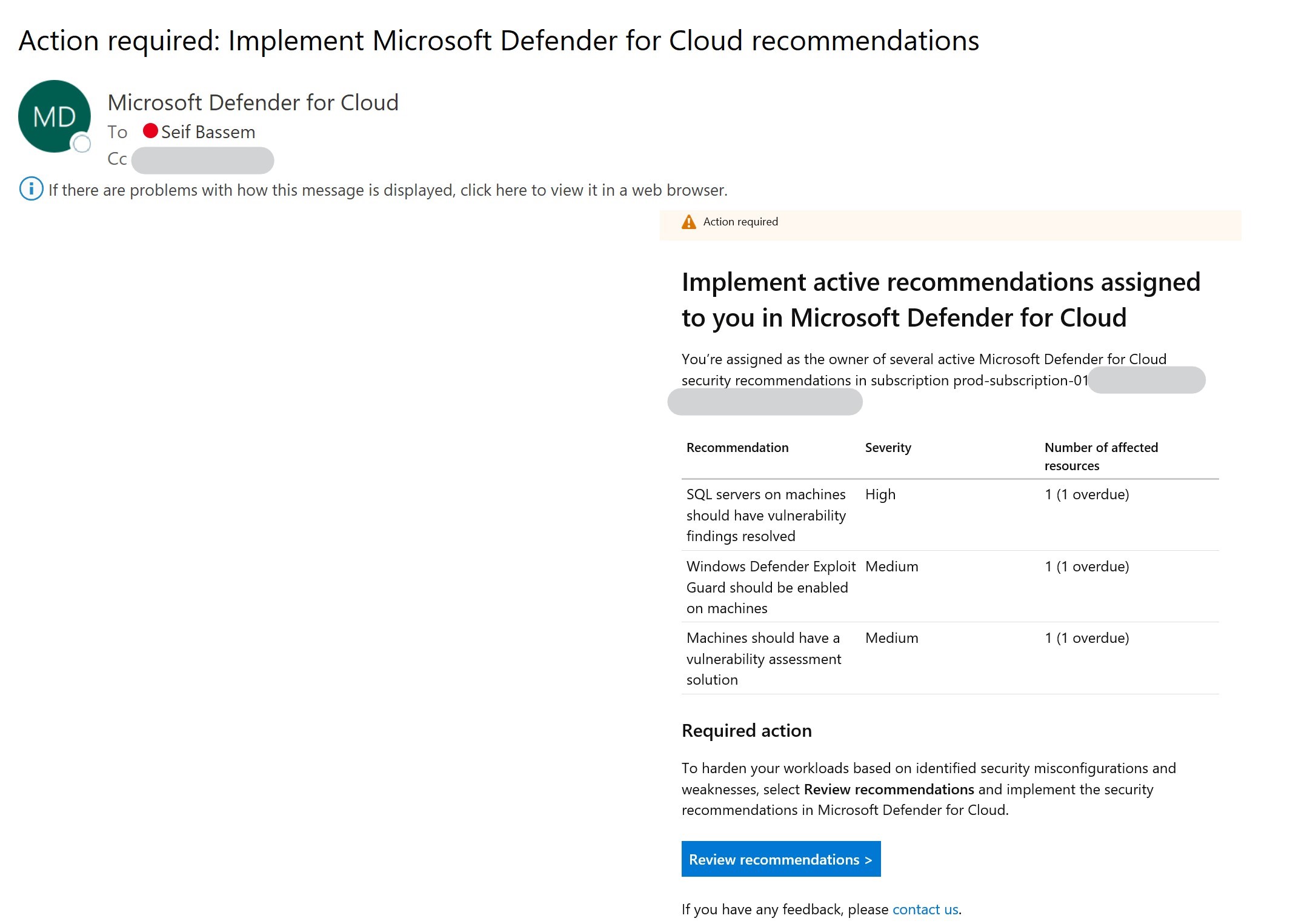
In addition to that, I started to get an email in a couple of days with my manager on it about my assigned tasks and timeframe.
Remediation process
After assigning owners and looking at the reporting, I need to start working on the remediation before the deadline. I will choose one of the recommendations on an Azure Arc-enabled server and start remediating it.
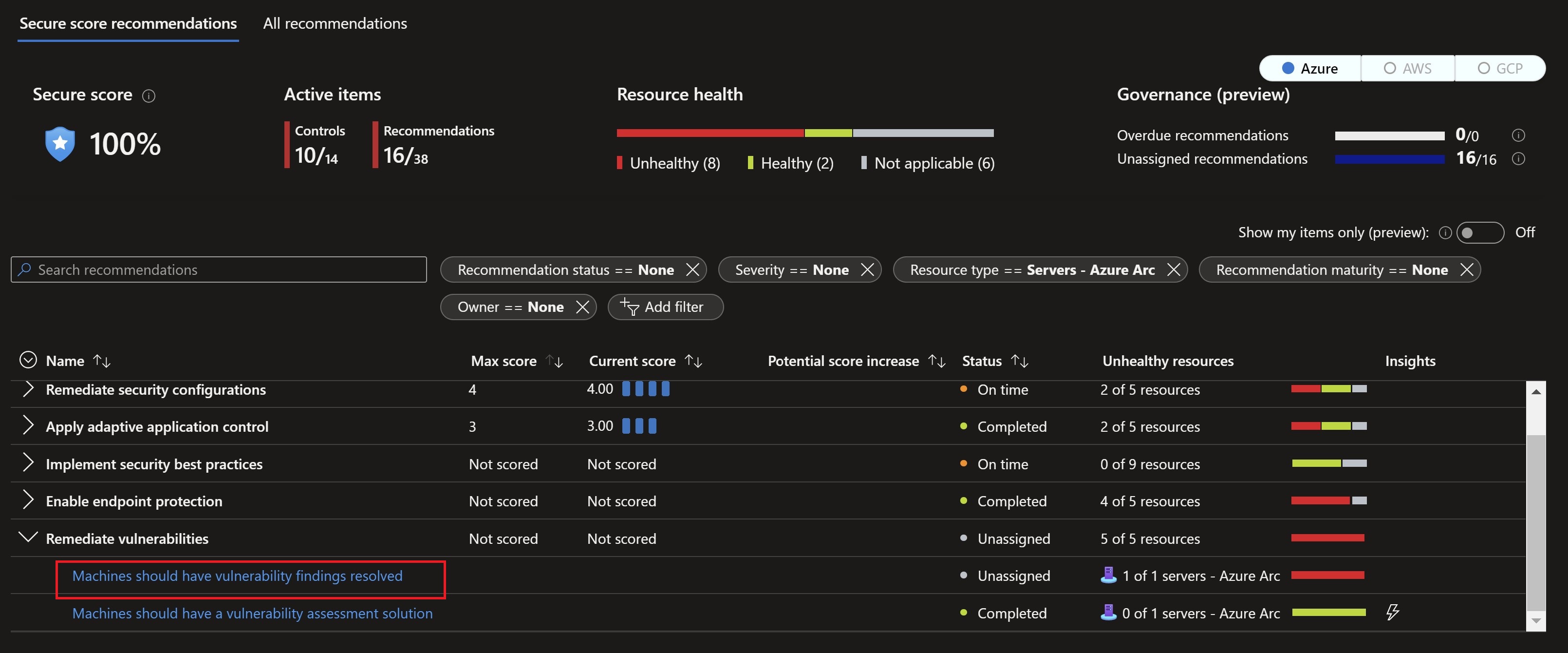
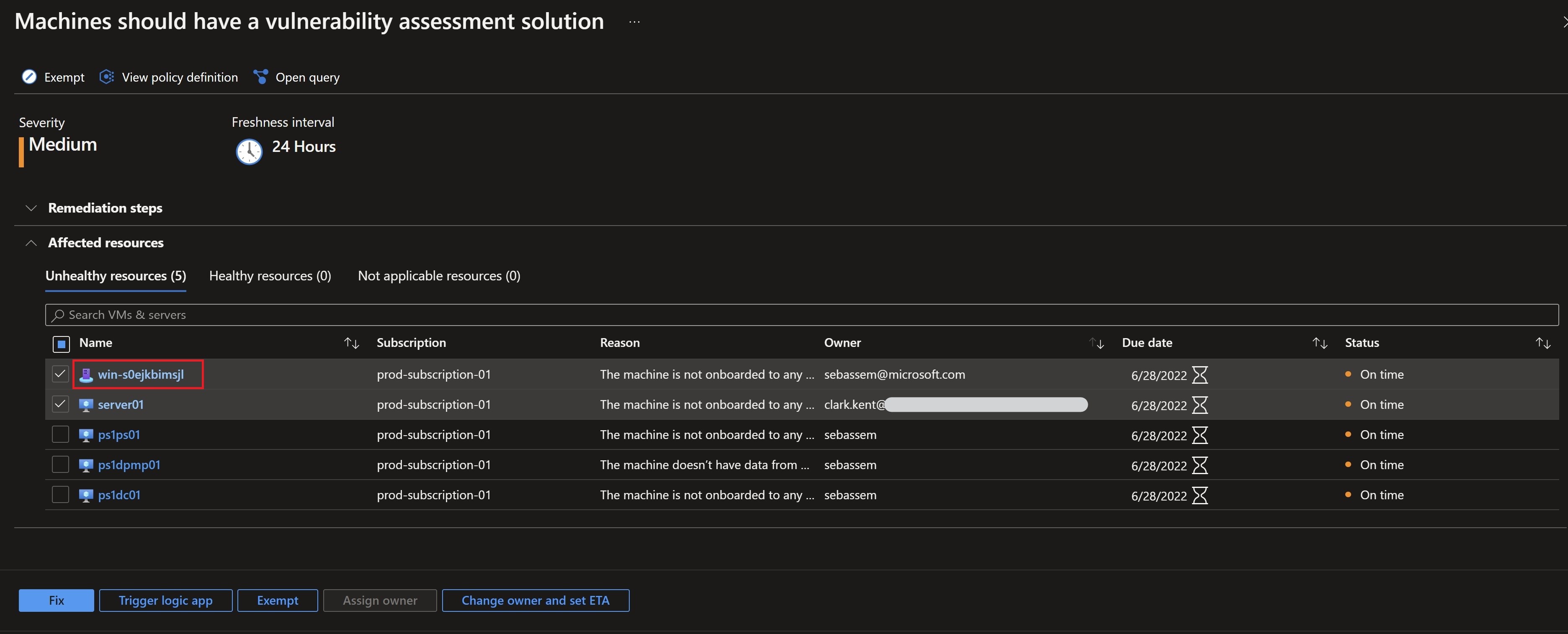
After waiting for some time for the vulnerability assessment solution to get on-boarded on the machine and start reporting back, I can see in the governance workbook that my task is now complete.
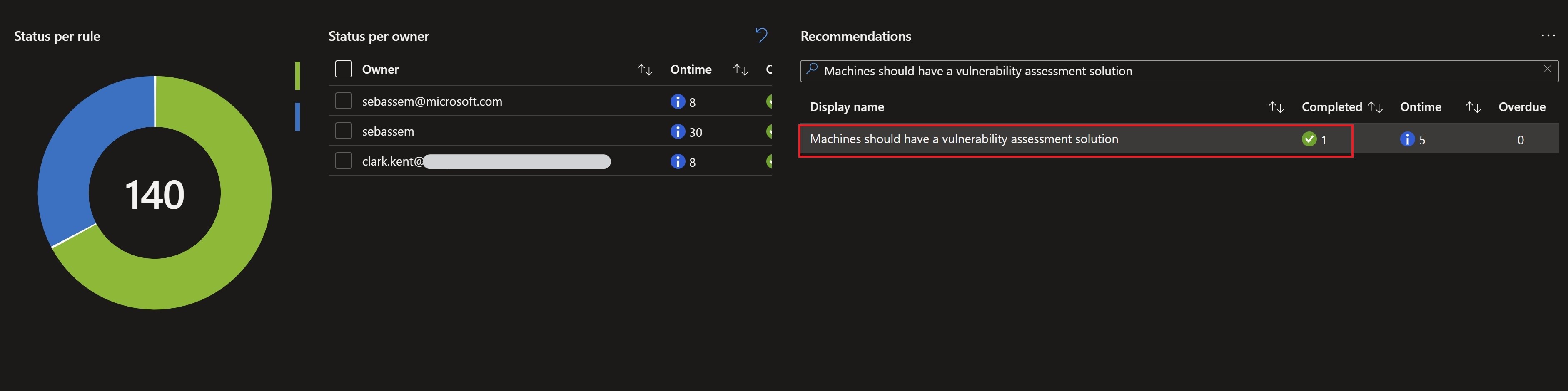
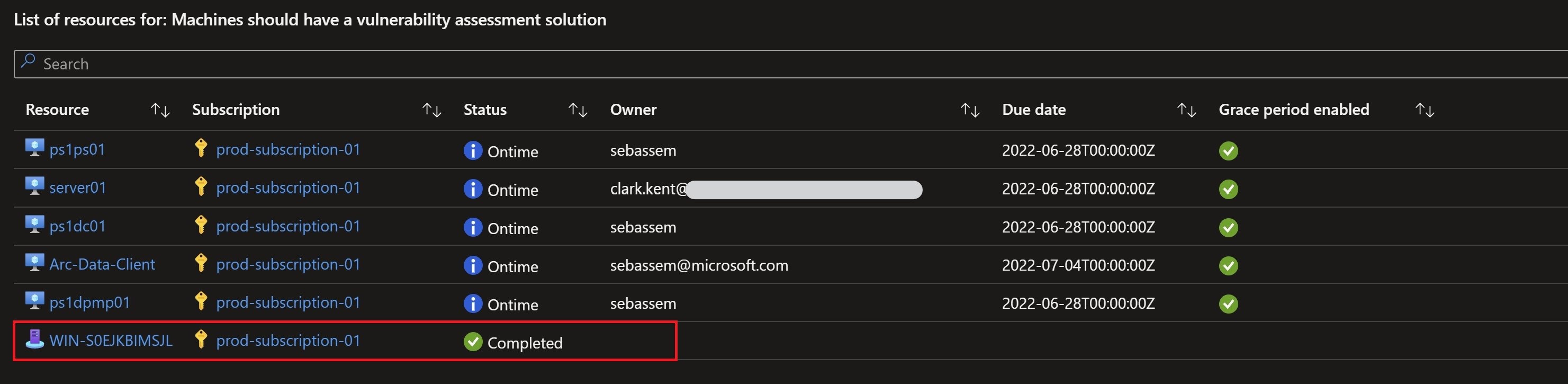
Recap
This is definitely a simple but very powerful feature to streamline the remediation process and drive accountability across system owners with enhanced reporting and weekly status emails. More information on this feature can be found here.
Share on:You May Also Like
A better way to enable Azure Defender
Azure Defender is Azure’s cloud workload protection tool ,it …
SSH into your Azure Arc-enabled servers from anywhere
A new capability has been introduced for Azure Arc-enabled servers …
Adding a user interface to your ARM templates
Have you ever deployed a complex ARM template with multiple parameters …